Silo for Safe Access was designed with enterprise needs in mind, and its SAML SSO integration allow seamless authentication without needing a PIN—just use your preferred Identity Provider (IdP)
With SAML SSO, the login process happens seamlessly in the background, so end-users get quick, hassle-free access without extra steps
Technical Details
Silo for Safe Access will work with any SAML 2.0 SSO implementation with some exceptions
SSO compatibility has been verified with the following Identity Providers:
- Duo
- Entra ID
- F5 BIG-IP
- Google SSO
- Microsoft ADFS
- Okta
- OneLogin
- PingIdentity (PingFederate)
- PingOne (Cloud)
- SecureAuth
System Requirements
- Silo Access Portal must be enabled
- TLS 1.2 protocol required
- Optional: Integrated Windows Authentication (IWA) for Windows OS
Important: Effective March 30, 2020, Authentic8 will only support TLS 1.2 connections, and will cease to accept TLS 1.1 connection requests. Any in-line network infrastructure connecting to our servers must also be configured to permit the use of the TLS 1.2 secure protocol
Configuration
We recommend reviewing your IdP's SAML SSO documentation on Service Provider (SP) configuration prior to working on the setup. This step should include identifying your IdP's SAML SSO URL values, and Base64 X.509 IdP Signing Certificate (.crt) to help streamline the process
Silo Portal Configuration
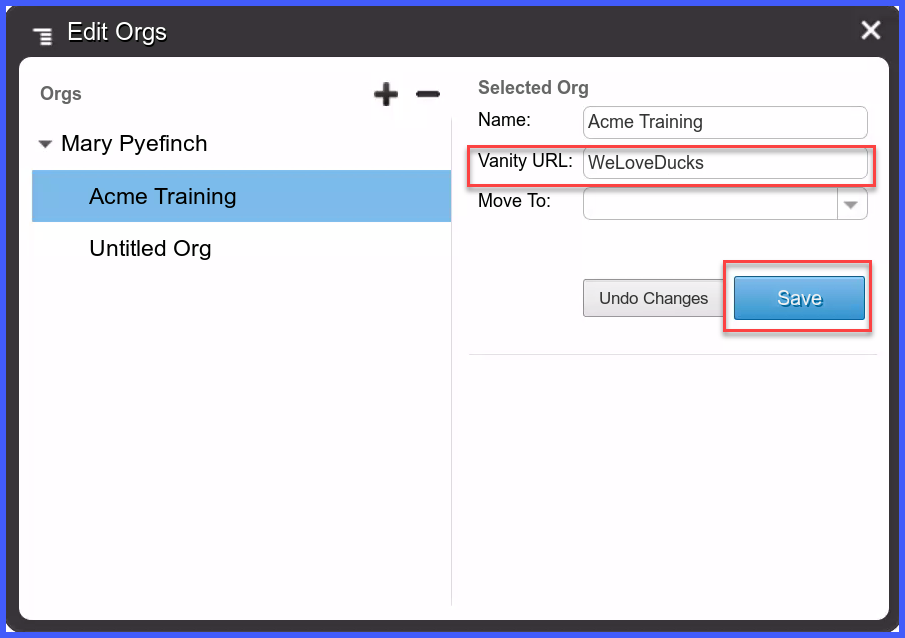
The Silo Portal configuration step consists of setting the Silo Access Portal (Vanity) URL; the Vanity URL must be defined in order for the SAML SSO configuration to work
It will serve as part of a custom URL string value to be used with SAML SSO authentication
Steps
From the Silo Admin Console, navigate to Users and Orgs section:
A. Click the Manage button
B. Select your ORG and click the Edit Orgs button
C. Enter a value in the Vanity URL field
D. Click Save
Silo Single Sign-On Configuration
A. From the Silo Admin Console navigate to the Single Sign-On configuration page
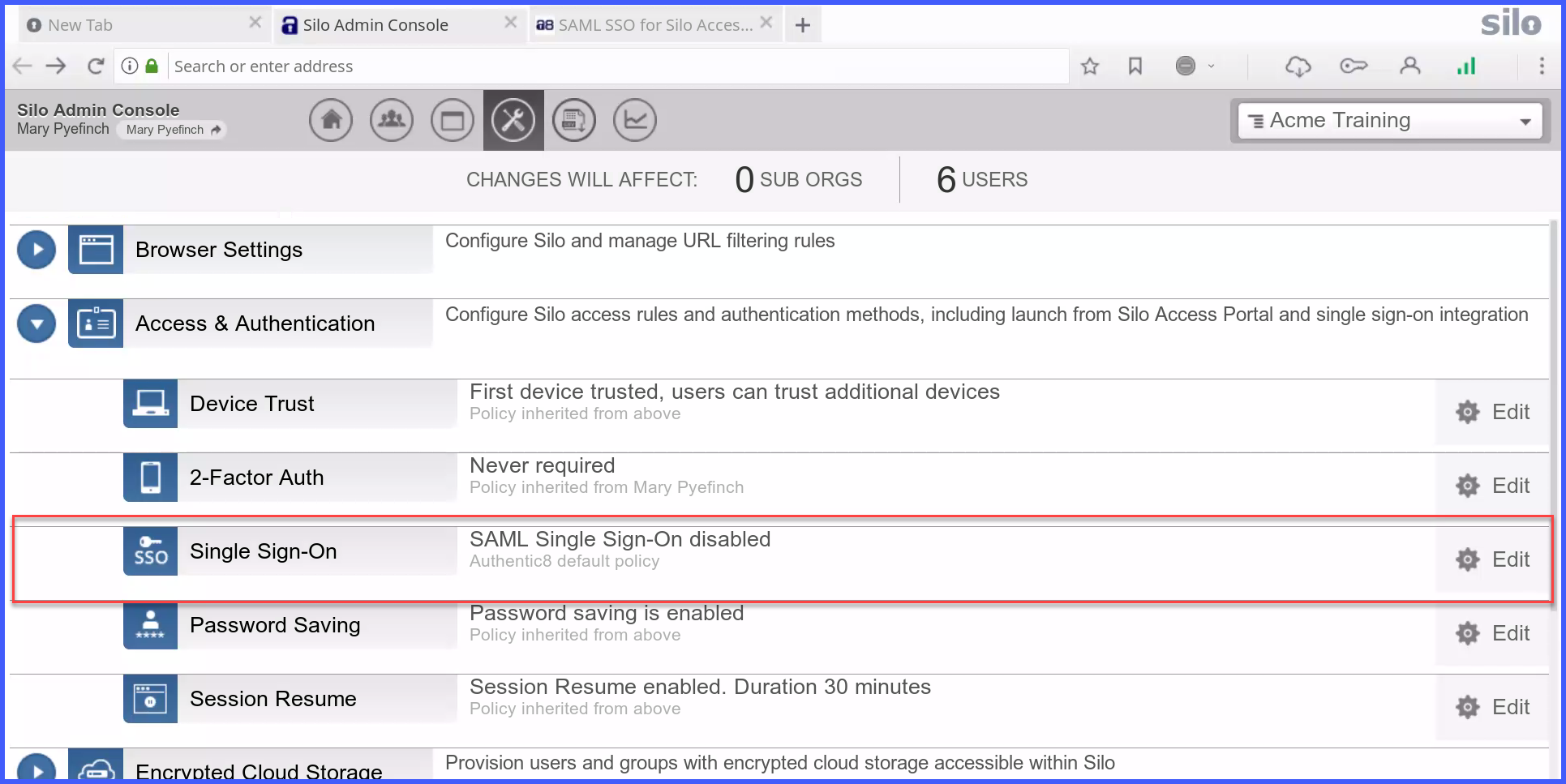
B. Enable SAML SSO and click Save

Identity Provider Configuration Steps
A. Copy and paste the displayed SP Entity ID and SP Post Back URL (ACS URL) values over to your IdP's configurationB. Download and install the Base64 encoded X509 IdP Signing Certificate (.crt)
More Info:- Please refer to your Identity Provider's documentation for specific instructions with entering the required SP URL values
- Authentic8 may have additional configuration support for other IdPs, which can be requested by contacting Support.
Silo Service Provider (SP) Configuration Steps
A. Obtain the applicable URL values from your IdP's SAML SSO configuration, and apply it to the Silo Admin Console
B. Upload the X509 IdP Signing Certificate file (.crt) in the Admin Console
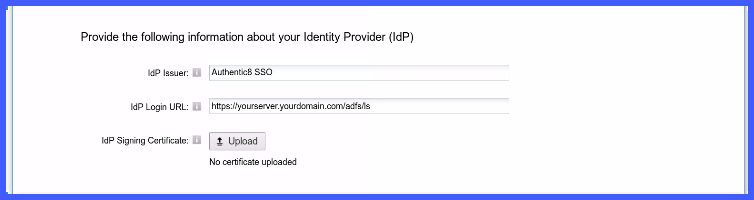
C. Save changes
Windows Registry
Please note that the FEATURE_BROWSER_EMULATION value is 2710 Hexadecimal not Decimal. The decimal value 10000.

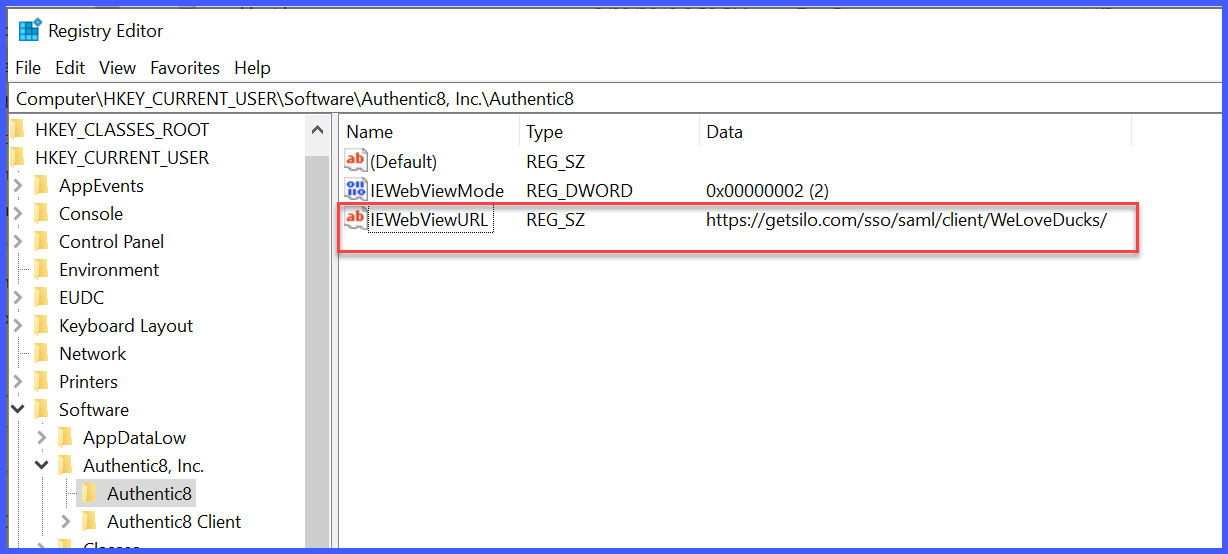
- IEWebViewURL = https://getsilo.com/sso/saml/client/<vanity_url_value>
The IEWebViewMode settings are defined below. The default setting for SAML SSO authentication is 2
IEWebViewMode Settings
When making the SAML registry changes, the IEWebViewMode setting needs to be set to the appropriate value
Value Authentication Method 0 Standard login (PIN) 1 A combined standard login and SAML option for testing 2 SAML
macOS plist Configuration
A. Open Terminal
B. If necessary, cd to /Users/<username>/Library/Preferences/ for com.authentic8.launcher.plist
C. Enter command as one continuous line:
defaults write com.authentic8.launcher WebViewUrl https://getsilo.com/sso/saml/client/<vanity_url_value>
D. Enter command: defaults write com.authentic8.launcher WebViewMode <1 or 2>
Examples:
Enter a value of [1] to display an optional [Use SSO] button
defaults write com.authentic8.launcher WebViewMode 1
Enter a value of [2] to enforce SSO authentication only
defaults write com.authentic8.launcher WebViewMode 2
E. To confirm the plist values, enter command:
defaults read com.authentic8.launcher | grep -i WebView
Optional: Integrated Windows Authentication (IWA) Settings
Configure your Internet Options to allow secure communication between the Silo client and your internal SAML SSO server
Steps
Control Panel
- Internet Options
- Security
- Local intranet
- Sites
- Advanced
- Type https://yourserver.yourdomain.com then click Add
Please contact Support for any additional questions
Silo for Safe Access was designed with enterprise needs in mind, and its SAML SSO integration allow seamless authentication without needing a PIN—just use your preferred Identity Provider (IdP)
With SAML SSO, the login process happens seamlessly in the background, so end-users get quick, hassle-free access without extra steps
Technical Details
Silo for Safe Access will work with any SAML 2.0 SSO implementation with some exceptions
SSO compatibility has been verified with the following Identity Providers:
- Duo
- Entra ID
- F5 BIG-IP
- Google SSO
- Microsoft ADFS
- Okta
- OneLogin
- PingIdentity (PingFederate)
- PingOne (Cloud)
- SecureAuth
System Requirements
- Silo Access Portal must be enabled
- TLS 1.2 protocol required
- Optional: Integrated Windows Authentication (IWA) for Windows OS
Important: Effective March 30, 2020, Authentic8 will only support TLS 1.2 connections, and will cease to accept TLS 1.1 connection requests. Any in-line network infrastructure connecting to our servers must also be configured to permit the use of the TLS 1.2 secure protocol
Configuration
We recommend reviewing your IdP's SAML SSO documentation on Service Provider (SP) configuration prior to working on the setup. This step should include identifying your IdP's SAML SSO URL values, and Base64 X.509 IdP Signing Certificate (.crt) to help streamline the process
Silo Portal Configuration
The Silo Portal configuration step consists of setting the Silo Access Portal (Vanity) URL; the Vanity URL must be defined in order for the SAML SSO configuration to work
It will serve as part of a custom URL string value to be used with SAML SSO authentication
Steps
From the Silo Admin Console, navigate to Users and Orgs section:
A. Click the Manage button
B. Select your ORG and click the Edit Orgs button
C. Enter a value in the Vanity URL field
D. Click Save

Silo Single Sign-On Configuration
A. From the Silo Admin Console navigate to the Single Sign-On configuration page

B. Enable SAML SSO and click Save

A. Copy and paste the displayed SP Entity ID and SP Post Back URL (ACS URL) values over to your IdP's configuration
More Info:
- Please refer to your Identity Provider's documentation for specific instructions with entering the required SP URL values
- Authentic8 may have additional configuration support for other IdPs, which can be requested by contacting Support.
Silo Service Provider (SP) Configuration Steps
A. Obtain the applicable URL values from your IdP's SAML SSO configuration, and apply it to the Silo Admin Console
B. Upload the X509 IdP Signing Certificate file (.crt) in the Admin Console

C. Save changes
Windows Registry
Please note that the FEATURE_BROWSER_EMULATION value is 2710 Hexadecimal not Decimal. The decimal value 10000.

- IEWebViewURL = https://getsilo.com/sso/saml/client/<vanity_url_value>
The IEWebViewMode settings are defined below. The default setting for SAML SSO authentication is 2
IEWebViewMode Settings
When making the SAML registry changes, the IEWebViewMode setting needs to be set to the appropriate value
Value | Authentication Method |
| 0 | Standard login (PIN) |
| 1 | A combined standard login and SAML option for testing |
| 2 | SAML |
macOS plist Configuration
A. Open Terminal
B. If necessary, cd to /Users/<username>/Library/Preferences/ for com.authentic8.launcher.plist
C. Enter command as one continuous line:
defaults write com.authentic8.launcher WebViewUrl https://getsilo.com/sso/saml/client/<vanity_url_value>
D. Enter command: defaults write com.authentic8.launcher WebViewMode <1 or 2>
Examples:
Enter a value of [1] to display an optional [Use SSO] button
defaults write com.authentic8.launcher WebViewMode 1
Enter a value of [2] to enforce SSO authentication only
defaults write com.authentic8.launcher WebViewMode 2
E. To confirm the plist values, enter command:
defaults read com.authentic8.launcher | grep -i WebView
Optional: Integrated Windows Authentication (IWA) Settings
Configure your Internet Options to allow secure communication between the Silo client and your internal SAML SSO server
Steps
Control Panel
- Internet Options
- Security
- Local intranet
- Sites
- Advanced
- Type https://yourserver.yourdomain.com then click Add
Please contact Support for any additional questions

